How to Create an Unhackable Password ?
To know how to create a strong enough password, we should know how hackers crack passwords.
Method 1: Guessing the password 🔗
The hacker try to guess the password and try it to find if it works or not. Guessing is based on collecting information about the owner of the account/password. The more accurate information you know the closer you are to the correct password.
Collected personal information are name, email, interests, field of study, nicknames, his/her son, his/her daughter, his/her partner, car brand, car plate number, phone number, landline number, street name, school name, college name, university name, birthday, his/her partner’s birthday, title, profession, favorite food, smartphone brand, favorite color, favorite animal, .. and other personal information that some people use in their passwords.
So, you should not use any of these in your password. If you insist on using any of them, make sure to change them a little bit.
Method 2: Brute force 🔗
Brute-forcing is the process of trying all password combinations based on its rules. For example; if the password has 4 digits, so brute-forcing is trying 0000, 0001, 0002,.. 9999.
To overcome this type of attack, you should choose a longer password. If the minimum length of password is 8, use a longer one; 10 or 12 characters.
Use uppercase letters, lowercase letters, numbers, and symbols such as @#$%&*.
Make sure to use letters from the first letters and others from the ending letters of the alphabet. That makes it harder to crack.
If you follow these tips above, your password needs years to get cracked.
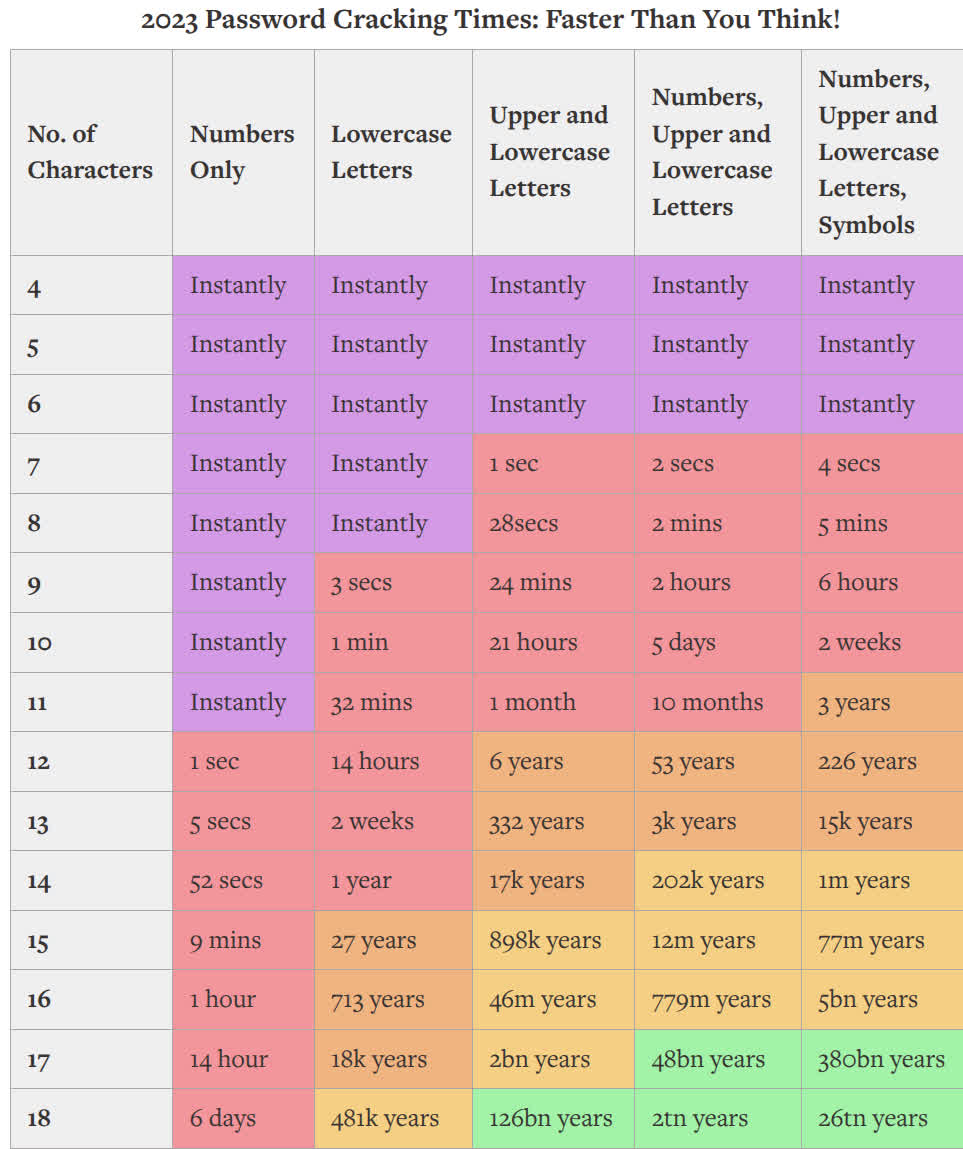 Source: BeCyberSmart: How Fast Can a Hacker Break YOUR Password?
Source: BeCyberSmart: How Fast Can a Hacker Break YOUR Password?
Method 3: Wordlists and Dictionaries of Breached Passwords 🔗
Millions of passwords and passphrases get leaked and breached online every year. These breached passwords get collected and cleaned into a wordlist or a dictionary or a rainbow table to be used by hackers in dictionary attack to crack a password hash. Hashcat is the known software tool in this field. Try not to use any of these passwords as your password of choice.
Method 4: Scamming and Phishing 🔗
Phishing is the process of creating a replica of the original website. The scamming is telling victims that that fake website is the original one. Hackers contact you telling various narratives to convince you to login via their link (of the fake website), so they get your credentials (email and password).
Creating a strong password will not protect you from this method of attack, but your awareness of these types of phishing strategies and scams is your defense mechanism.
The general way to detect the phishing webpage is to look at the page URL and realize if the domain is the exact original domain or a fake one.
The general way of detecting the scams is the rule of “too good to be true”. If someone contacted you about a prize, job, paid task, .. that is too good to be true, it is. I mean, it is not true, it is a scam.. it is a trap for you to fall in.
I hope you enjoyed reading this post as much as I enjoyed writing it. If you know a person who can benefit from this information, send them a link of this post. If you want to get notified about new posts, follow me on YouTube , Twitter (x) , LinkedIn , and GitHub .