Vulnerable WordPress Release Not Yet Fixed
Today, I checked my WordPress website inside my shared hosting > CPanel > WP toolkit. I ran into this screen.
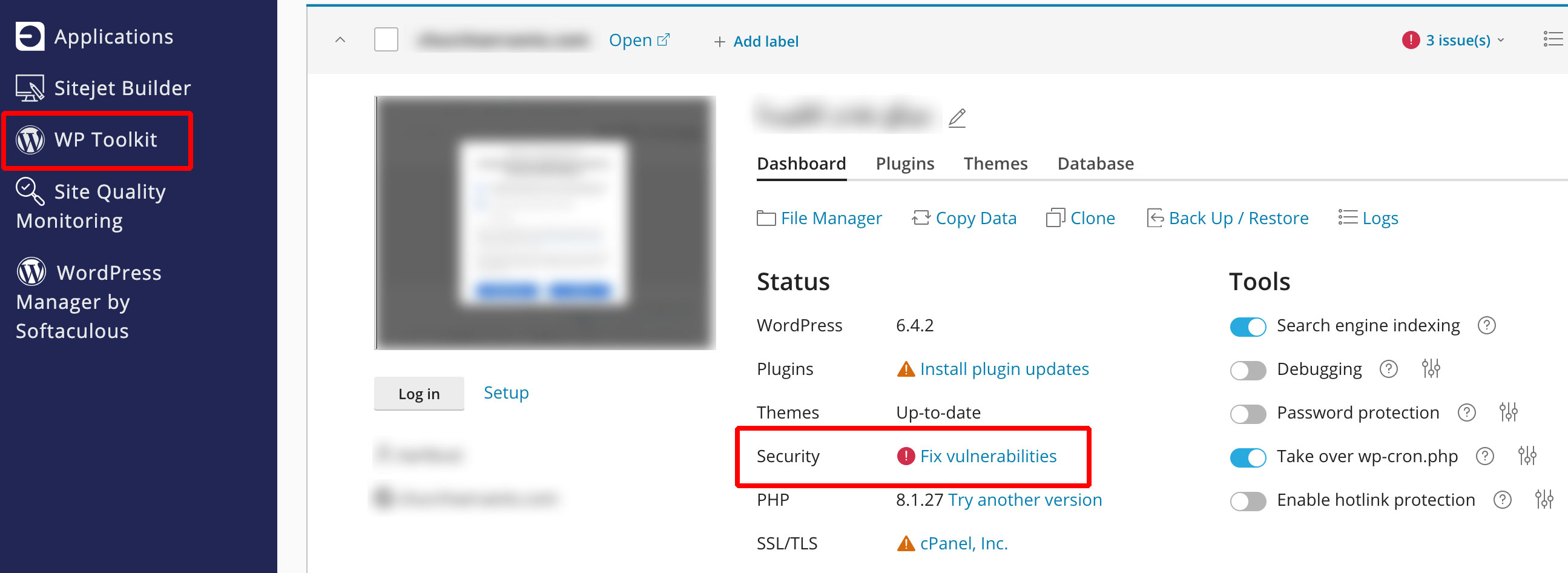
It says Fix vulnerability in security. I clicked on it. A security scanning process stated. After the scan completed, It stated that my current WordPress core release is vulnerable. It is affected by unauthorized blind server-side request forgery vulnerability.
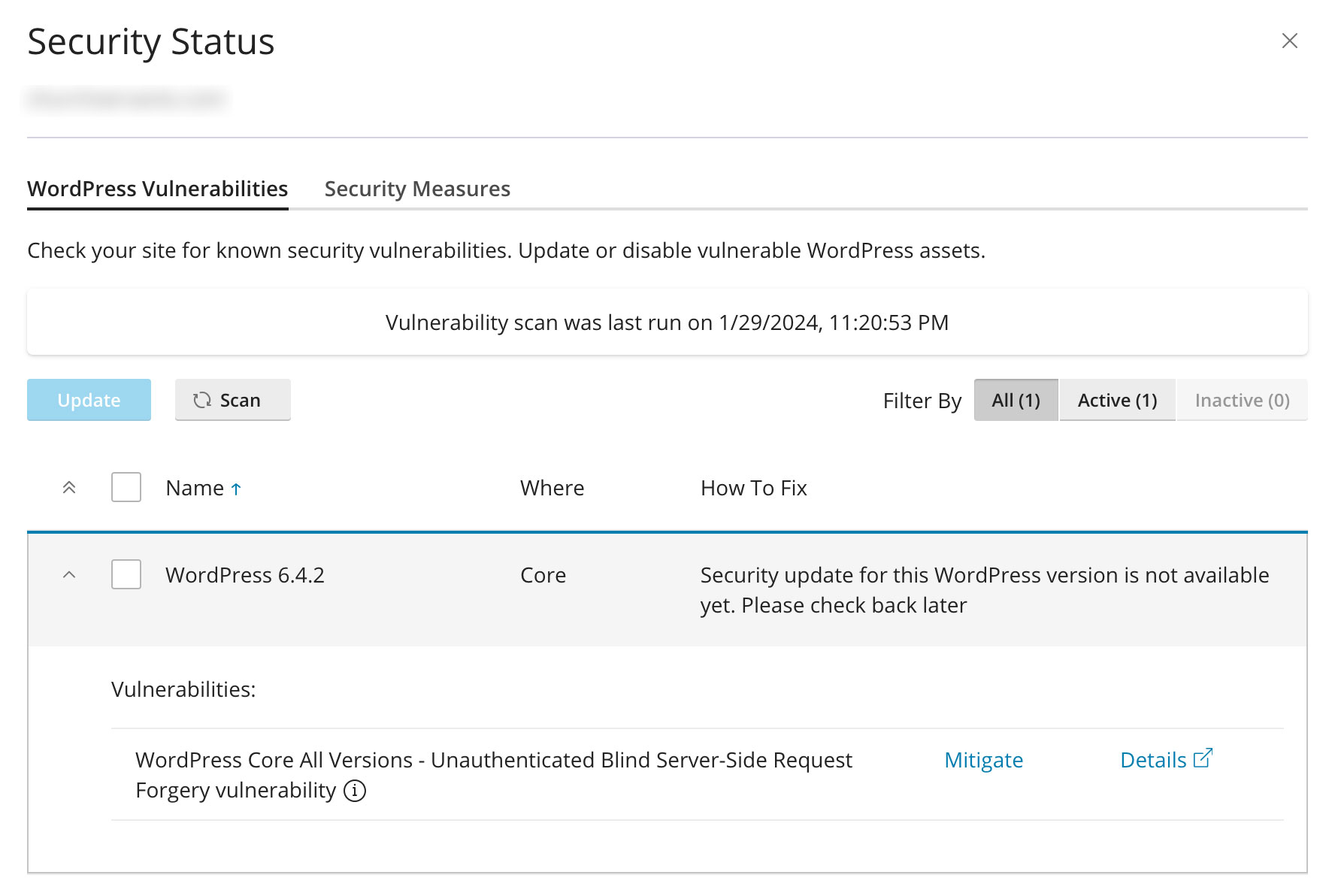
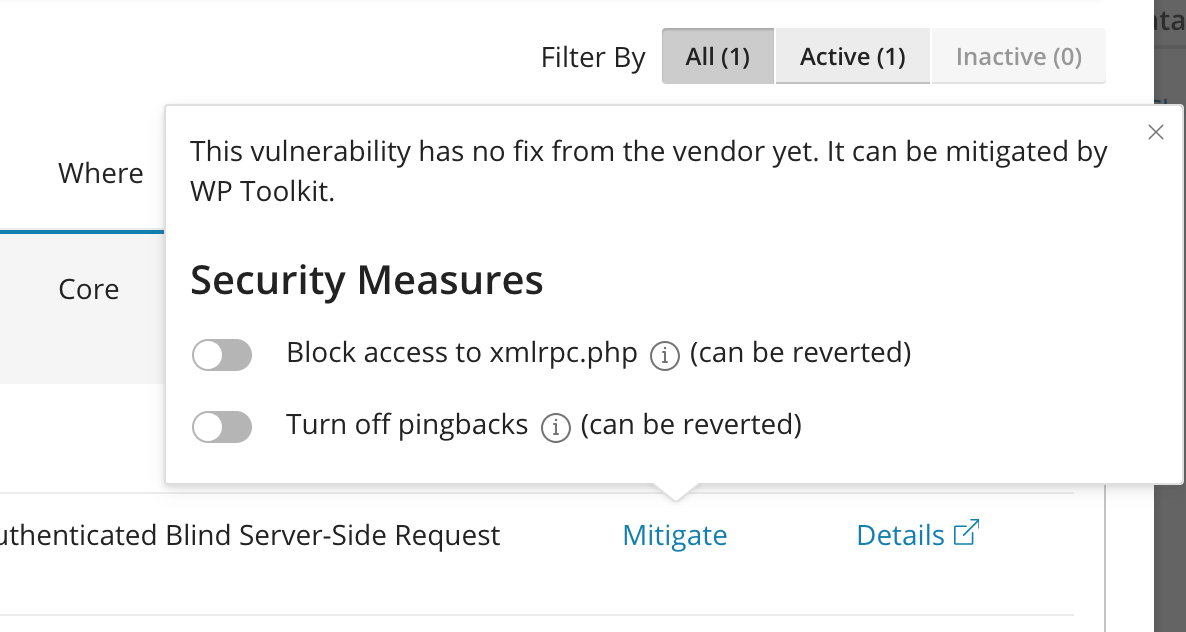
I clicked on mitigate to reduce the risk of the vulnerability if it is exploited.
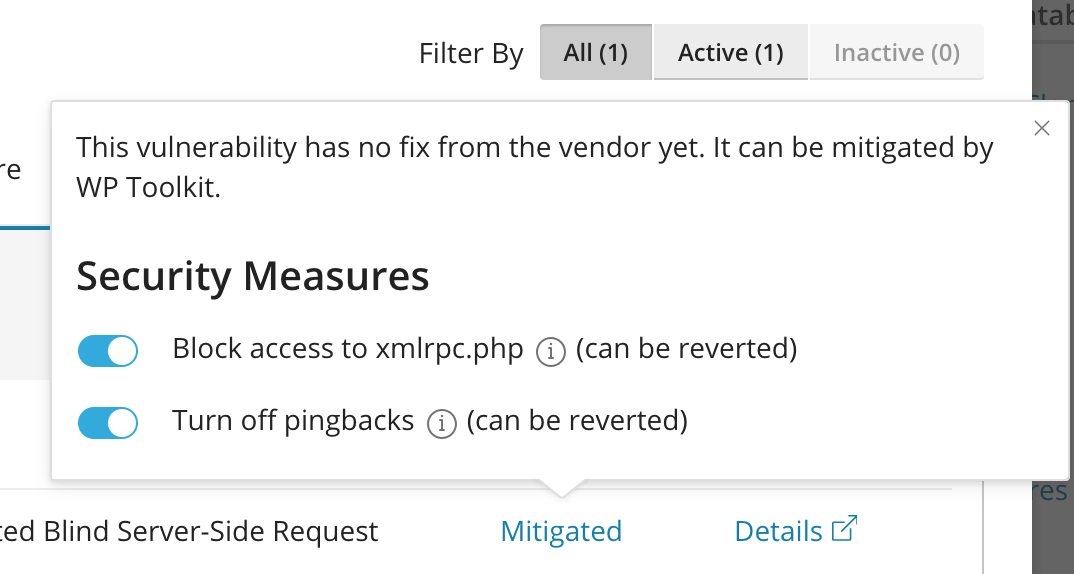
I turned on both security measures as you can see below.
If you want to learn more about this vulnerability, visit patchstack.com and read more about the vulnerability on WordPress official website .
What are the risks of exploiting it? 🔗
If the severity is high,
- Attackers can exploit this vulnerability to perform unauthorized requests from your WordPress site without needing any login credentials.
- This opens doors to a wide range of potential attacks, including:
- information leak: Stealing sensitive data like database credentials, user information, or internal server files.
- Denial-of-service (DoS) attacks: Crashing your server or other internal systems by sending them overwhelming requests.
- Lateral movement: Gaining access to other systems on your network by exploiting internal vulnerabilities.
- Code execution: Uploading and executing malicious code on your server, potentially taking complete control.
But if severity is low,
- The actual impact depends on:
- Exploitability: The exploitability of the vulnerability might be limited depending on your server configuration and the attacker’s skills.
- Value of target: if your server doesn’t hold valuable information or systems, the attacker might not gain much benefit.
- Mitigations in place: Having adequate security measures like firewalls, intrusion detection systems, and up-to-date software can significantly reduce the risk.
How to deal with this vulnerability? 🔗
Update WordPress to the latest release 🔗
Update WordPress core as soon as the update is available.
Disable XML-RPC 🔗
If your site doesn’t rely on XML-RPC functionality, disable xmlrpc.php file by clicking on “mitigate” button in WP Toolkit as you saw above in the images/screenshots.
Disable Pingbacks 🔗
You can consider disabling pingbacks in your WordPress settings, although this might affect some social features. You can disable Pingbacks by clicking on “mitigate” button in WP Toolkit.
Implement security measures 🔗
Install plugins or configure your server to restrict outgoing traffic and monitor for suspicious activity.
Migrate to a static site generator (SSG) 🔗
SSGs work on your local machine (a.k.a your laptop computer), then you run a command to generate the static webpages, then upload these static webpages to a server to serve them to visitors. Using static webpages is great for SEO and security, but this strategy lacks interactivity and dynamic content such as comments and creating posts online/on the server. If you are good with creating new posts on your laptop, then pushing them to the server to publish them without comment section, this SSG strategy is good for you. I - myself - use Hugo SSG to create and publish this website you are reading on.
Update : 31 Jan 2024 🔗
An update of WordPress 6.4.3 released today to fix this vulnerability and other bug fixes. Make sure to upgrade to the latest version of WordPress.
I hope this post helps you. If you know a person who can benefit from this information, send them a link of this post. If you want to get notified about new posts, follow me on YouTube , Twitter (x) , LinkedIn , and GitHub .